How to Securing Linux system
In this article we shall focus on simple ways to make Linux systems more secure, from attackers point of view.
Disabling ports
All the unused ports need to be disabled. Ports such as 80/http, 22/ssh, 21/ftp if they are not in use. In Kali Linux all ports are disabled by default on boot. To disable port starting on boot use systemctl disable [service name].
systemctl disable ssh if on Debian systems and systemctl disable sshd on RedHat like systems. A remainder do only to those ports that are not being used.
Removal of unused kernel modules
Unused kernel modules should also be removed from system they may contain exploit weakness.
To remove kernel modules you us :sudo rmmod [Linux Kernel module name]
Use of firewalls
On ports that are being used you can use the software firewalls, such as the iptables or firewall-cmd. But new upgrades iptables has changed little bit.
sudo iptables -I INPUT -m recent --set --name SSH
sudo iptables -I INPUT -p tcp --dport 22 -m state --state NEW,ESTABLISHED -m recent --update --seconds 60 --hitcount 4 -j DROP this command will block/drop NEW or any connection established previously if it attempts more then 3 connections under one minute.
![]()
Use of administrative accounts
Use of administrative user accounts is highly supported, locking the root using the passwd. passwd -l root this will prevent any user to try logging to the root account. A user with administrative privileges can only run that command.
You can use my previous article on how to edit the sudoers file and gain administrative privileges https://www.hackerxone.com/2021/08/25/how-to-edit-the-sudoers-file.
On boot
When a Linux boots with the standard procedures, it can be very easy for one to change the parameters and gain access to root.
Firstly, open /etc/default/grub file with you favorite editor having the sudo privileges. Find timeout and change from original value to 0 seconds.
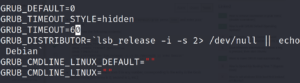
the update grub with sudo update-grub to the new configurations to /boot/grub/grub.cfg
In this article, we have simple security basics of Linux security.
